PaperCut NG/MF can authenticate users against Azure AD using Secure LDAP. This means you do not need an on-site Active Directory server; you can use directory services hosted in the cloud.
LDAP (Lightweight Directory Access Protocol) directories usually store information about users and groups in an organization. Microsoft’s LDAP interface has been hardened to support authentication across less-secured networks, such as the internet.
To synchronize your user data with Azure AD Secure LDAP:
Before you begin
You will need:
-
A current Azure AD subscription that has AD Domain Services enabled.
-
A certificate to enable secure communication:
-
Use PKCS#12 (PFX in Microsoft terms). For more information on PKCS#12 certificates, see PKCS 12
-
2048-bit is recommended
-
Password protected (that is, includes the private key)
-
-
Users and groups in Azure.
-
AAD DC Administrator login credentials for the domain to sync.
Step 1. Enable Secure LDAP
-
Log in to Azure as an AAD DC Administrator.
-
In the Search bar, search for and select Azure AD Domain Services. The Azure AD Domain Services page is displayed listing your managed domain.
-
Select the service you want to synchronize.
-
In the navigation pane, under Manage, select Secure LDAP.
-
In Secure LDAP, select Enable.
-
In Allow Secure LDAP access over the internet, select Enable.
-
Click the folder icon next to .PFX file with secure LDAP certificate. Specify the path to the PFX file with the certificate for secure LDAP access to the managed domain.
-
Enter the Password to decrypt the .PFX file. Provide the same password you used when exporting the certificate to the PFX file.
-
Click Save.
-
In the navigation pane, under Manage, select Properties.
-
Copy the Secure LDAP external IP address.
For more information, see Configure secure LDAP (LDAPS) for an Azure AD Domain Services managed domain .
Step 2. Set the primary sync source
-
Select Options > User/Group Sync. The User/Group Sync page is displayed.
-
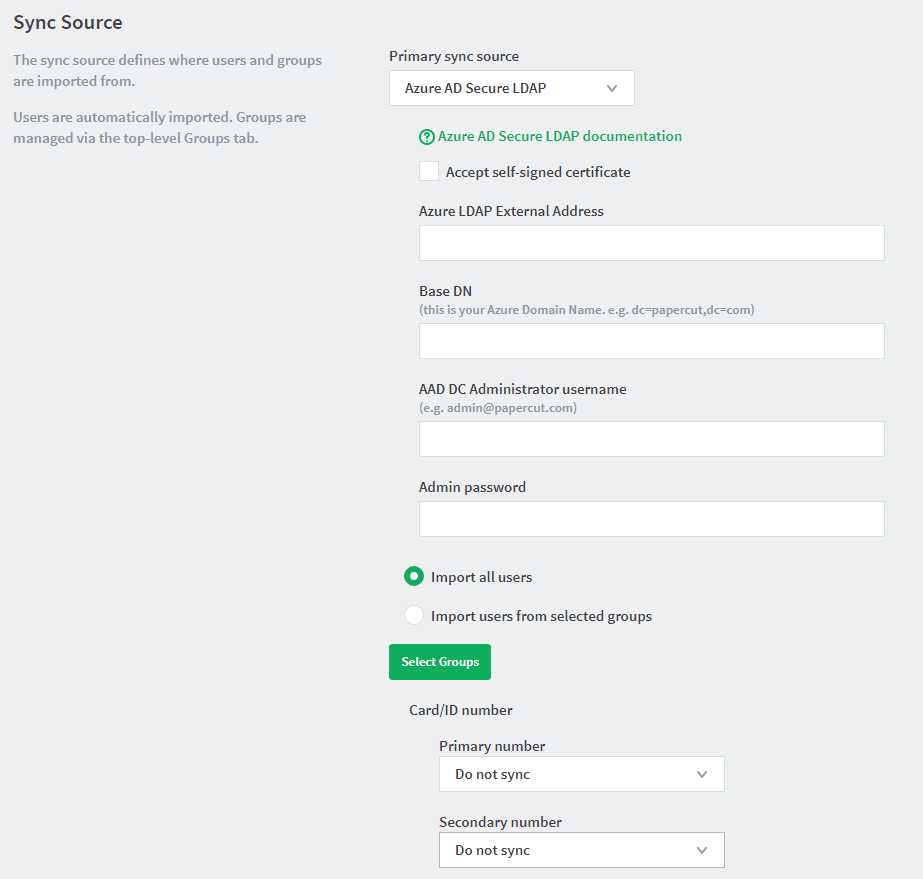
In the Sync Source area, in Primary sync source, select Azure AD Secure LDAP.
-
Complete the following fields as required:
-
Accept self-signed certificate—Select this check box if you are using a self-signed certificate that does not need to be validated. If you are using a certificate signed by a trusted authority, clear this checkbox.
-
Azure LDAP External Address—Your LDAP external address copied above from Azure AD Secure LDAP.
-
Base DN—Your Azure DNS Domain Name. This is the equivalent of the “suffix” config setting of the OpenLDAP server. For example, if the domain hosted by the LDAP server is “domain.com”, then the Base DN might be
DC=domain,DC=com. The format of the Base DN can differ significantly depending on the configuration. Some older Novell eDirectory installations require a blank Base DN to operate. Some examples:DC=myschool,DC=edu,DC=auDC=myorganization,DC=comOU=OrgUnit,DC=domain,DC=comDC=local -
AAD DC Administrator username—The Azure Active Directory DC administrator username. For example, admin@papercut.com .
-
Admin password—The password for the above user.
-
-
Select the users to import:
-
Import all users
-
Import users from selected groups—If you select the option, click Select Groups; then select the groups/OUs you want to import. This option is useful if the domain contains old users or users who do not print.
-
Step 3. Add card/identity numbers
Card and ID numbers are used as an alternative to usernames/passwords for authentication at software Release Stations, or at hardware terminals attached to photocopiers. The card/ID number can also be searched in the user quick-find in the User List page. See User card and ID numbers for more information.
In PaperCut NG/MF, you can associate one or two unique card/ID numbers with each user. These are known as the primary and secondary card/ID number. You can automatically import or generate these card/ID numbers for each user.
Often card/ID numbers are already assigned by other systems, in which case you must import these numbers into PaperCut NG/MF from Active Directory or LDAP. Unlike other fields, such as full name and email address, there is no standard field used exclusively for card numbers. For this reason, PaperCut NG/MF allows specifying the field from which to import the card/ID number.
You can add card/identity numbers in the following ways:
Generate random card/ID numbers
PaperCut also allows you to generate a random card/ID number for either the primary or secondary card/ID number. To auto-generate card numbers:
-
In the Sync Source area, complete the following fields:
-
Primary number—select Auto-generate random ID (if blank).
-
Length—enter the number of digits.
Short numbers are easier to remember and faster to key in, but it is also easier to guess someone else’s number. If your number is too short, PaperCut cannot generate sufficient numbers to cover all your users.
-
-
Click Apply.
Import the card/identity number from LDAP
LDAP provides a very flexible way to store user related information. The fields available depend on LDAP server being used and how that is configured. Many LDAP servers also allow administrators to create custom fields to store additional custom user information. You should consult your LDAP server’s documentation or talk to your LDAP administrator to understand which LDAP field stores the user card/ID number.
-
In Primary number, select Sync from AD/LDAP field.
-
In AD/LDAP field name, enter the name of the field containing the card/ID numbers. By default, PaperCut NG/MF uses the
employeeNumberfield to retrieve the primary card number. This is a standard LDAP field, but if this is not suitable, you can choose any valid LDAP user field. -
If required, import the secondary Card/ID numbers.
-
In Secondary number, select Sync from AD/LDAP field.
-
In AD/LDAP field name, enter the name of the field containing the card/ID numbers.
-
Extract the card/id number from an LDAP/AD field using a regular expression
The vast majority of sites store the full card number in a single field in AD/LDAP. In this situation, you do not need to use a regular expression (regex) to extract the card number. A regular expression is required only under some specific circumstances, including:
-
The field contains more than just the card number. For example, if the field contained a card number and student number separated by a comma (for example, 12345678,0003456).
-
The multi-valued LDAP/AD field contains multiple values and only one represents the card number. For example, some third-party authentication management systems store external IDs (like card numbers) in a single multi-valued LDAP field.
To use a regular expression to extract the card/id number:
-
In the Sync Source area, select the Apply regular expression to extract primary/secondary card number from AD/LDAP check box.
-
Enter the regular expression used to extract the card number. The regular expression must contain a capture group (represented by parentheses), that represents the part of the field that the card number is extracted from.
The simplest way to create a regular expression is to start with one of the following examples.
Example regular expressions to extract card numbers
| Regular Expression | Description |
|---|---|
([\d]+) | Extracts the first sequence of digits. For exampl, if the field contains 12345678,005678 then 12345678 is extracted. |
([\d]{5}) | Extracts the first sequence of 5 digits. For example, if the field contains 12345678 then 12345 is extracted. |
=([\d]+) | Extracts the sequence of digits after the = character. For example, if the field contains 12345678=56789" then 56789 is extracted. |
([\d]+)::abc | Extracts the sequence of digits preceding the text ::abc. This is a common notation when storing identities in a multi-valued field in LDAP. The ::abc notation is used to indicate the different identity types. In this example, if the field contains 1234::xyz 5678:qrs 9876::abc then 9876 is extracted. |
For more information on regular expressions and a test tool, see http://www.fileformat.info/tool/regex.htm . If you need assistance, please contact support.
Step 4. Set the secondary sync source (optional)
Enabling a secondary sync source allows PaperCut to merge the results from two independent sources. Examples of where this is useful include:
-
A school with an Active Directory domain for the majority of users and a separate LDAP server that is used and managed by one department.
-
An organization with a new LDAP server and an old legacy LDAP server with separate but unique users who have not been migrated to the new server.
-
A university with an Active Directory for the Windows student workstations and an Open Directory for the staff Mac workstations.
When enabled, PaperCut queries both sources to find users and groups. Usernames are treated as globally unique, so the same username existing in both sources is treated as the same user (in this case, the details for the user are merged, with the primary sync source taking priority). If there is an error connecting to or synchronizing against either source then no actions takes place.
To set a secondary sync source:
-
In the Secondary Sync Source (Advanced) area, select the Enable secondary sync source check box.
-
Complete the secondary sync source details as described above. These fields are the same as those for the primary sync source.
Step 5. Set the sync options
The options listed in the Sync Options area control how the synchronization will take place.
-
In the Sync Options area, select any of the following options as appropriate:
-
Update users’ full name, email, department and office when synchronizing—if a user’s details in PaperCut do not match those in the synchronization source, update the details in PaperCut NG/MF.
-
Import new users and update details overnight—synchronization automatically occurs each night at approximately 12:55 am. This option never deletes users from PaperCut.
-
Delete users that do not exist in the selected source—deletes users from PaperCut if they no longer exist in the selected synchronization source.
This option affects only users added via the synchronization source (for example, the domain) and does not delete Guest and anonymous user management . Users that do not exist in the Sync source are deleted only when you manually synchronize (click Synchronize Now).
This option does not delete users when automatically synchronizing overnight.
-
-
To test the operation, click Test Settings.
A Testing sync settings popup dialog box displays the details of users and user groups that will be modified (updated, added or deleted) when the actual sync operation is run.
-
Click Apply.




Comments