Be safe and in control of your print environment
In many ways, print security is just like house security or building security. In building security we make an effort to control who can enter, and often when and where they can go. The same can apply to printing. Who’s allowed to use your Multifunction Devices (MFDs)? Should anyone be allowed to pick up your print jobs?
This article applies the Physical-Procedural-Technical approch to security, and discusses how they can be applied in a network printing context. You’ll see how often simple changes to printing flow can help improve security.
Thinking security: Physical-Procedural-Technical
Imagine your organization’s building, or even your home or school. There’s probably been a fair amount of effort spent on defining who can enter it and when. Printing security (and document security) can often have the same complexity and demands.
To introduce some structure into this topic, let’s look at the three main categories of controls you can use to defend information systems — namely physical controls, procedural controls, and technical controls. Now keep these three categories in mind while you plan your print security to help design an appropriate level of security for your environment.
Physical security
Physical security relates to the tangible environment that you’re trying to secure (for example, how big should the lock be on the door?) In a printing context, examples of physical controls include:
- Where you put your printers or MFDs — For example, in an open area, or locked away in a secure office/region?
- How users authenticate at the printer or MFD — For example, must users swipe an ID badge? Or use a username and password?
- Hardening for the physical environment — For example, public libraries or Universities often need to lock paper trays to avoid paper theft, or even securely lock network cables to avoid network bypass.
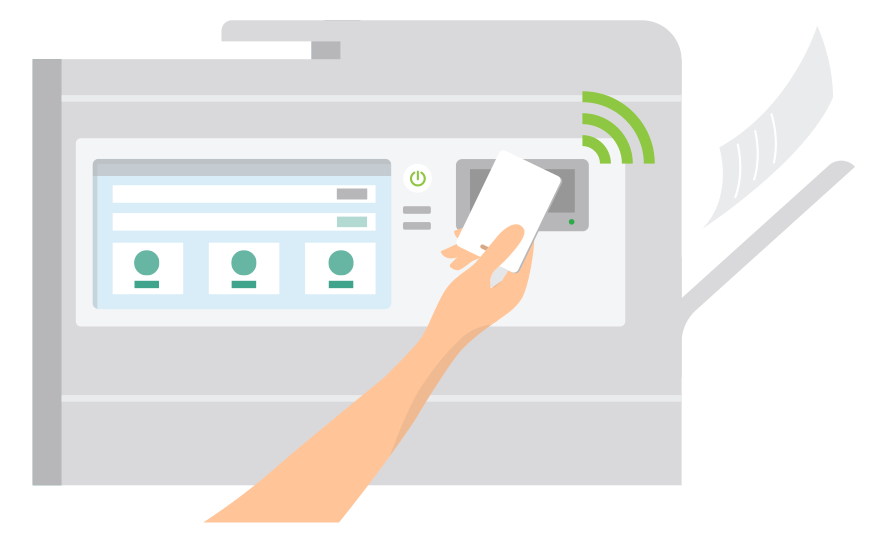
Procedural security
Procedural security involves creating a culture of security, and putting into action the practices and processes required to obtain that security. A good example of a culture of security exists in building security with a practice like “Don’t let tailgaters follow you through any secure door.” In the printing environment, good procedural security includes:
- A process to manage who can access printers and copiers — For example, anyone with a valid network login or door access card.
- Managing when someone can access a printer — For example, access rules that define the time of day someone or a group can print.
- Awareness and training of printer use and document security — For example, what’s appropriate to print, and how to handle personal identifying information.
- Print audit logs and reporting — For example, who can access audit logs and how the information should be used.
Technical security
Technical controls use technology to improve security or implement better countermeasures. In a build security context, it might be a choice to use video cameras to monitor access. In a printing context, some modern technology security measures include:
- Print protocol selection — For example, are your print jobs encrypted in transmission and can they be intercepted?
- Card-based printer access — For example, can you use the card readers that use the same technology as your door access card system to secure printer access and secure print release.
- Two-factor authentication (2FA) — For example, are cards secure if lost? Combining a PIN and a Card will help here.
- Watermarking and digital signatures — For example, are jobs tagged with a watermark so they are more secure after printing?
- Limited printing access — For example, limit use of color, maxium document sizes, etc.
- Spool file encryption — For example, avoid data theft.
Five-point checklist to get you started
As explained above, you can take print security as seriously as any other area of security. Here is what we consider are the five musts for best practice around print security.
| Task | Why? | Action | Product | |
|---|---|---|---|---|
| 1. | Ensure printing and document collection is an authenticated service | You would not give the key to your building to someone without knowing who the person was! | Implement secure print release. | PaperCut MF PaperCut Hive PaperCut Pocket |
| 2. | Ensure print authorization is easy | If it’s really hard to get in the door, people do silly things like prop it open! Make printer access easy. | Make secure print release easy with access cards (PaperCut MF) or mobile phones (PaperCut Pocket). | PaperCut MF PaperCut Hive PaperCut Pocket |
| 3. | Have you got speciality printers? Decide who can access them. | Access to the lunchroom for everyone, but not the boardroom! Some specialty printers are expensive to run and access should be restricted. | Set access control and policies on your printers at a user level. | PaperCut MF PaperCut NG PaperCut Hive PaperCut Pocket |
| 4. | Leverage existing identities | Have one key rather than a keyring with many keys. Keep user identity simple and central to help prevent mistakes. | Sync with directory services like Active Directory or other directory services, and implement card self-association. | PaperCut MF PaperCut Hive |
| 5. | Look at audit trails in all forms | We all wish you had the audit logs after an incident! | Understand all audit logs, primarily the print log and the application activity log. | PaperCut MF PaperCut NG PaperCut Hive PaperCut Pocket |
Real world examples
There are hundreds of topics about the thankless task of taming your printers. We have taken best practices from some key industries to give you examples of how people are using print security 'out in the wild'.
Education
A large metropolitan university wanted to improve their community engagement, and started by offering services to the public through their libraries using BYOD and guest printing. With a large take-up of the service, the project was initially deemed a success. However, students had realized that if they printed as a “guest” they could print for free (ouch!). By implementing PaperCut Mobility Print with BYOD authentication ensured that bona-fide guests (with supplied temporary credentials) could easily print while maintaining proper controls on normal printing.
At the same university, after ‘free printing’ incident there was increased attention into print volumes and inspection of print log data. One of the administrators also saw that one of the janitors was occassionally copying a large amount of documents at 6am. Implementing access control and timed printing helped to ensure that only people that should have access to printing could do so at this time.
Healthcare
A large healthcare organization was desperate to get their name out of the headlines after three high-profile incidents where Patient Health Information (PHI) was misplaced. Yikes! With PaperCut, they were able to take control of risk around the printed document by combining secure print release using staff ID badges, and watermarking the print user’s name on each printed page.
This combination of active security control and passive behavior modification paid immediate dividends, with printed PHI only being collected by the authorized user who printed it, and those same users taking more personal responsibility for securing documents that could so easily be traced back to them.
Small Business
Government / Local Council
Security audits are never fun, and when a state government department was pulled up for allowing some sensitive documents to transit unencrypted over internal networks as part of their print workflow, they had to act fast.
The solution was two parts PaperCut, one part good networking practice. First, they set up PaperCut Mobility Print to ensure all printed data from the BYOD devices was encrypted in flight. Next, they configured the PaperCut Application Server with a department signed certificate to significantly reduce the chance of man-in-the-middle attacks. Then, on the networking side, they moved the printer IP addresses onto a separate VLAN, and voila! End-to-end protected print data, isolated from all other client and server attack surfaces.
Features in more detail
The following content explains a number of the features referenced in the examples above.
Printer Access Control (who, when, where)
Often seen as the first line of defense, controlling access to the printers or copiers/MFDs in your environment can be an important initial security goal. Access control can be anything from ‘you’re not allowed to print to the finance printer’ to ‘you’ll need to prove it’s you standing at the printer, in order to pick up your print job’.
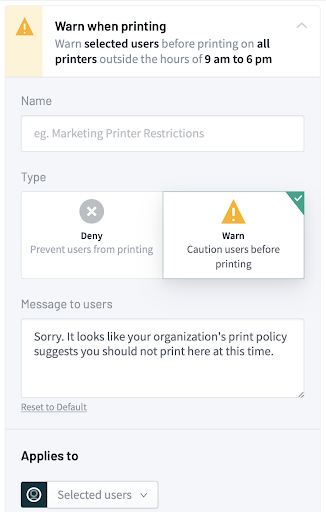
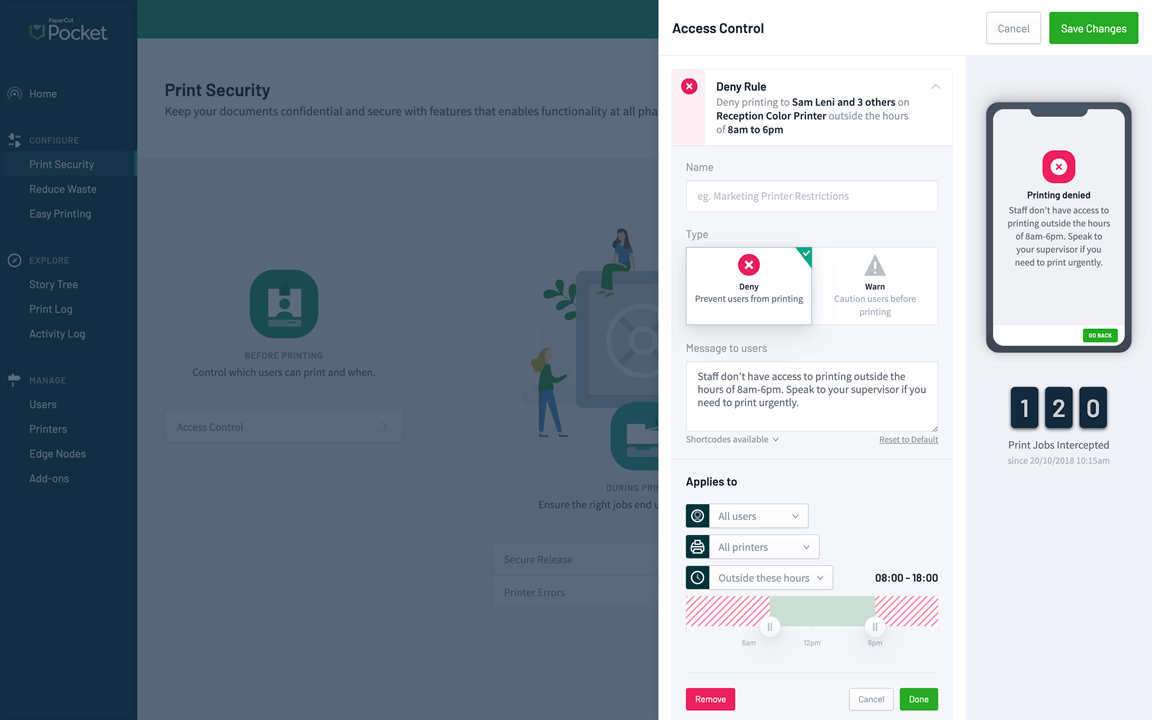
With PaperCut Hive and PaperCut Pocket the restrictions are simple and customizable. Want to start things off by just warning users for the first month, before denying them printing completely later down the track? Or maybe deny all printing for those night owls trying to print after 11pm. That’s all possible through the admin interface by configuring device notifications for the user.
Within PaperCut NG and MF, there are a number of ways to use the filters and restrictions. The simple interface lets you decide who should be able to print to which printer, and whether certain documents should be denied. For example, you might not want people printing out emails so you can deny the ability to accidentally print out private communications. The print scripting functionality lets you get gritty and granular around who is denied, who is warned, and even how they’re communicated to — email or popup for example!
However, life is sometimes not as simple as allowing or denying a user (or group) per printer. If you want to let your users print from their phones, laptops, and other devices, PaperCut Mobility Print has the ability to configure access to those on a particular subnet. Not only do you secure and control your environment by doing this, you also make the experience a lot better for the person printing. They now only see the list of relevant printers for the building they’re in.
So many document leaks come from someone printing to their ’last’ printer through muscle memory — and only later realizing they’re across the campus from their printed job.
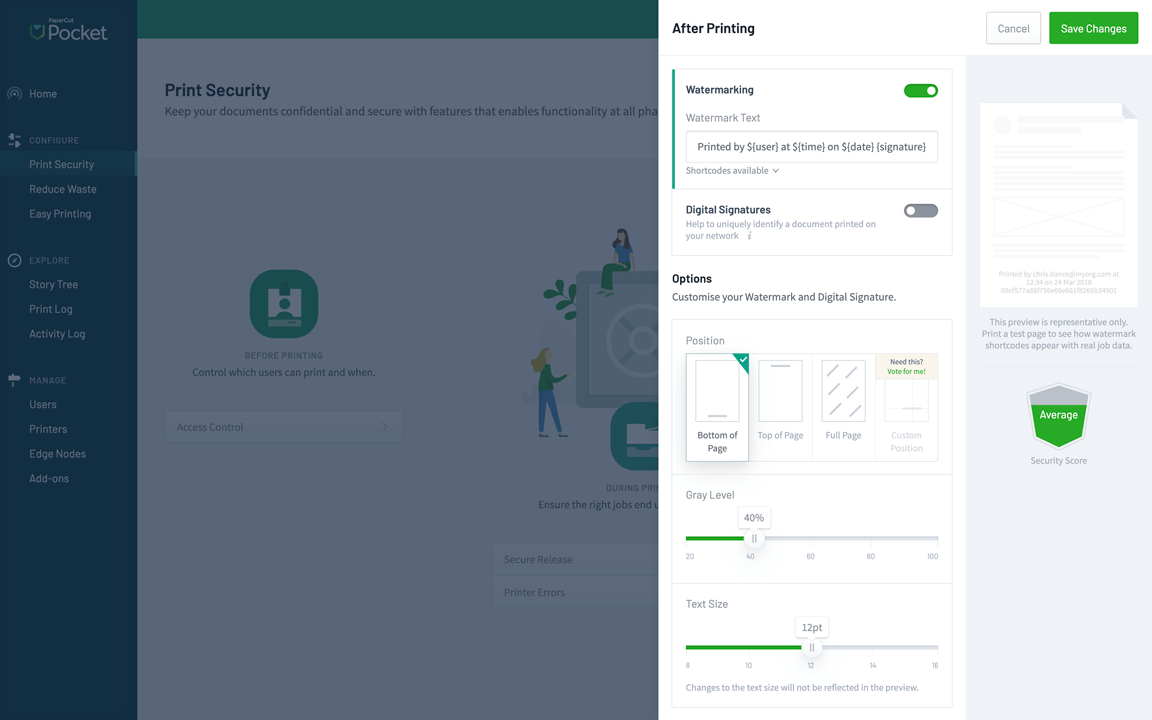
Watermarking
Watermarking is a key security tool for tracking down runaway documents, and it also helps change the behavior of your users. With documents visibly personalized, gone are the days of people just leaving them on the printer because they’re anonymous — everyone just became a little more print-responsible.
The watermark could be a username and date, or could be as cryptic as a digital signature, allowing you to track the exact instant of print in your job logs.
PaperCut NG and MF watermarking and digital signatures are configurable through the printer options, while PaperCut Hive and PaperCut Pocket have the same options in the ‘after printing’ section. All products have the capability of positioning the watermark wherever you’d like on the page, and also picking the visibility level — allowing you to choose between clandestine or clamoring!
Secure print release
Secure print release is arguably one of the key building blocks of your environment. It allows you to almost completely eradicate any ’lost print job syndrome’. By knowing who’s standing there waiting to pick up their print job, you know that they’re only picking up what belongs to them — a bit like getting your coat from the cloakroom — with the added advantage that you can turn your coat grayscale on collection to save money.
PaperCut NG allows secure print release from a release station. You just walk up to a computer, log in as yourself and release all (or some) of your print jobs to the printer next to you. PaperCut MF makes things even more simple since it combines the MFD (the printer) and the release station. PaperCut Hive and PaperCut Pocket include the same features, and out-of-the-box allow you to release your print job with your mobile phone.
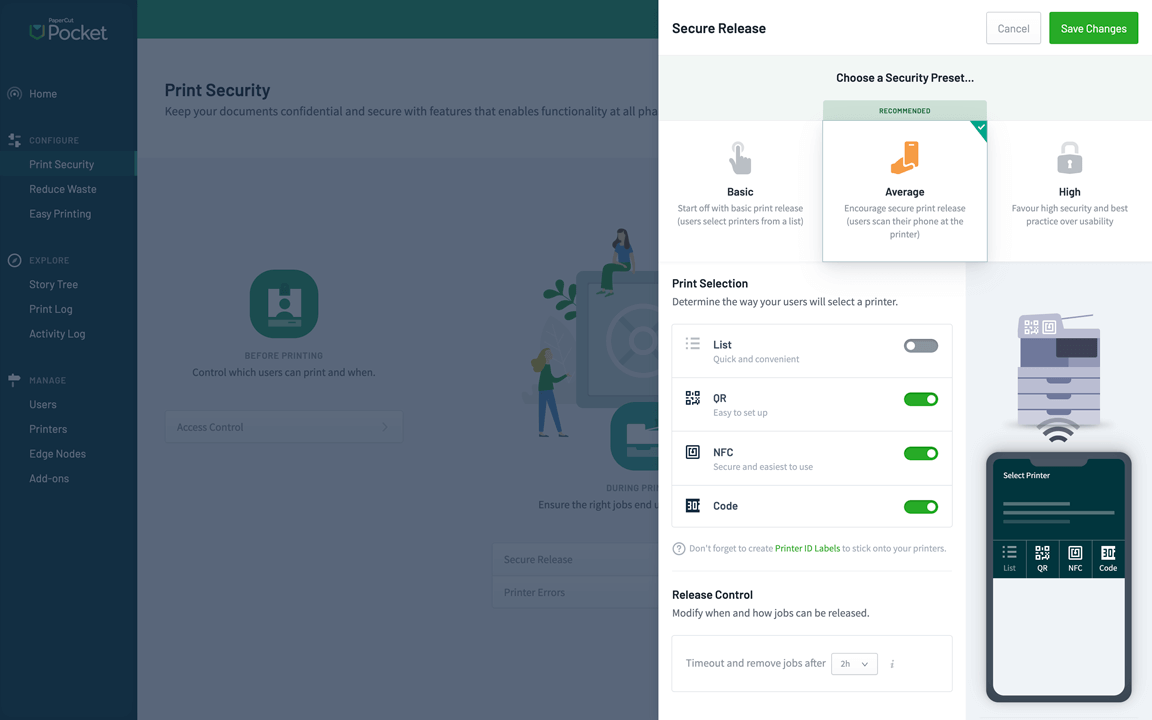
NFC, QR codes, security access cards, badges, usernames/passwords, IDs and PINs — even your thumbprint or a scan of your iris can release your print jobs for you, all depending on how secure you want to be!
Spool file encryption
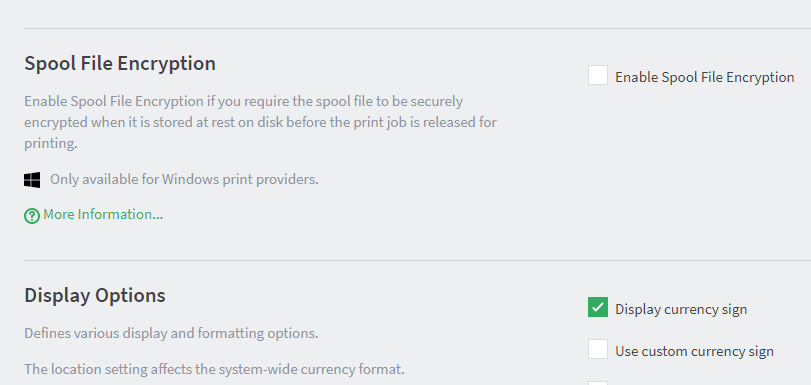
Bolstering the PaperCut NG/MF security story, spool file encryption is for organizations that want to safeguard sensitive and confidential documents while they’re waiting to be printed. Spool File Encryption is a useful way to add an additional layer of security to print jobs in the hold/release queue.
For organizations that are sensitive to anyone being able to access the printer spool files and get hold of the job information, Spool File Encryption helps avoid data theft. All jobs are encrypted using the AES-256-GCM algorithm while they are waiting to be released for printing. Our solution provides data integrity, on-the-fly encryption, and uses dynamic multi-part keys. This means that every single print job has a separate encryption key, preventing a global attack on all print jobs. This feature is currently available for Windows only.
Print policies
Everyone has a different view of what print policies should be. Luckily we don’t make you fit anything pre-defined, you can set as much or as little as you want. And if you want the policy to be short and simple, it can be — goodbye long, formal policy documents. Simply encouraging the right printing behaviors by enabling certain rules and suggestions can sometimes do the trick on its own.
In fact a large number of customers start with no policies — printing’s free for all! Over a period of time the customers monitor and see how much printing is done, what types of documents are color vs grayscale, what department is printing in simplex vs duplex, etc. From that information they then form an idea of what policies to try out.
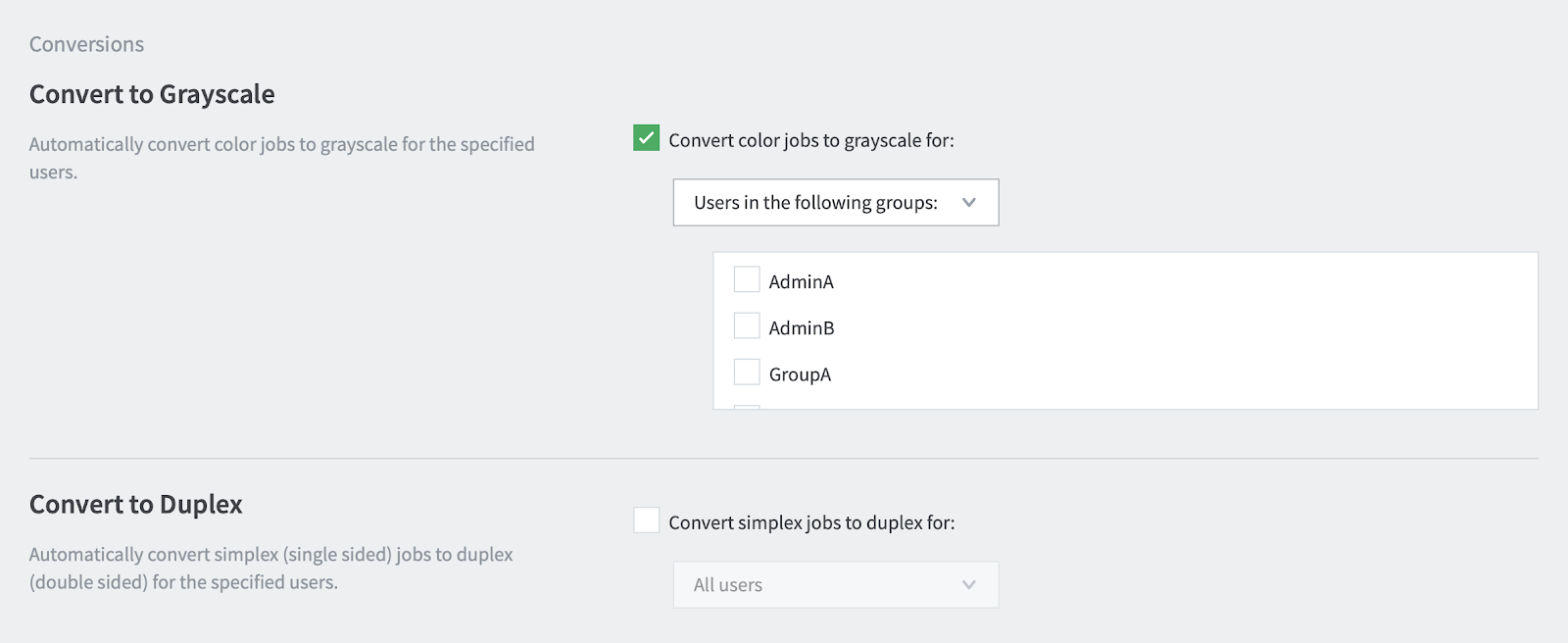
Even when you set your policies, you can implement them as harshly or suggestively as you like. For example, you could have a popup suggesting that the 20 page color PDF could be printed as grayscale (AND they could save $5 as a result). Or you could deny the document completely because it’s in simplex mode and not duplex!
There’s a myriad of options for policies, all easily configured under the Filters and Restrictions section in PaperCut NG and MF. Even just setting up charging for prints, or setting up user quotas will help your users think more about the cost of printing options, and ultimately the environment! Within PaperCut Hive and PaperCut Pocket, print policies settings are found under ‘Reduce waste’ and ‘Print security’ sections of the admin dashboard.
BYOD, Mobile, and Guest printing (and PaperCut Mobility Print)
Often the biggest headache for a SysAdmin or IT guardian is what happens when people bring their own laptops/phones/computers/watches into the mix? It’s almost expected that you can do on your phone whatever you can do on your organization’s laptop — and PaperCut can help you keep up to speed with the latest printing requirements.
PaperCut Mobility Print takes the headache out of connecting the myriad of devices that you can’t control — your users can now print in a consistent and intuitive way, without calling the help desk to get things set up. Even better, when you link PaperCut Mobility Print with PaperCut NG or MF, you can apply all of the other benefits like user management, policies, and secure print release to the otherwise unknown devices on your network.
PaperCut Hive and PaperCut Pocket offer the same print-from-any-device ease of use and functionality, and both can allow guest use, too. Need to allow conference or meetup attendees to print a couple of pages when they come to visit? We’ve got you covered.
Want to know more…?
Here are some links you might find helpful:
- Did you know you can control printer access based on time?
- There’s a whole section on Secure Print Release in the Paper NG/MF Help Center, including how to install and configure a release station.
- Find out how to choose the right mobile and BYOD print strategy for your organization.
- There’s a wealth of information in the Mobility Print Help Center, including plenty of FAQs.