How to secure cloud print documents with PaperCut
Security is one of the biggest questions hovering around any cloud print service. Whether using a fully-hosted (multi-tenant SaaS) solution or a single-tenant instance that’s self-hosted in a private cloud, there is the concern that print documents traveling via the internet could get hacked by nefarious cyber pirates. Unfortunately many people don’t think printing is a security concern - but the evidence proves otherwise.
Let’s immediately set your mind at ease (and scare away those data-loving Long John Silvers). Your print document won’t make its way into the big scary internet with any of PaperCut’s cloud solutions.
For all our products, from a private cloud setup for PaperCut MF with your chosen data center that you manage, to our public-hosted PaperCut Hive and PaperCut Pocket infrastructure, the system keeps documents away from the public internet: you don’t need to secure what you don’t have.
Self-hosted (single-tenant) cloud print management is as secure as on-premise print management. The concern of print data privacy is more relevant to fully-hosted (multi-tenant SaaS) cloud solutions, which call for a level of security designed for the public internet.
Data security is designed into everything PaperCut builds, but it’s doubly important for print management in the cloud. Security and privacy is at the forefront of our engineering before we write a single line of code.
Put on your comfy shoes, because we’re going to walk you through the security architecture of our product suite.
Edge Mesh: PaperCut Hive and PaperCut Pocket
The beating heart of our cloud-native solutions - PaperCut Hive and PaperCut Pocket - is the Edge Mesh.
The Edge Mesh is a resilient, secure, and self-healing local network of edge nodes (devices on the local network). It receives print jobs from users, processes, encrypts, and releases them to the desired print device.
Our Edge Mesh architecture was built with security in mind following shift-left principles: the practise of moving testing and preventing defects from right (towards the end) to left (at the beginning) on the timeline of software development.
When a shift-left mindset is taken into print architecture design this obvious question comes up: I’m at my desk and I can see the printer, why would my document have to go all the way to the internet and back again to print? Is this not just an unnecessary step that potentially exposes me to a data leak? That’s why we decided to build the Edge Mesh.
In PaperCut Hive and PaperCut Pocket, our cloud acts as a coordinator for configuration of your printing environment, rather than the gatekeeper of the documents themselves. The delivery of print jobs remains local and point-to-point thanks to the Edge Mesh.There is a caveat to these points. Many organizations do want to facilitate off-site printing. That might be someone printing at home and collecting their job when they get to work. Or someone at a cafe printing and then collecting when they get to the office.
This is done with the magic of the Cloud Node, an optional component that can be enabled (by default). For remote printing, or special cases such as a job transferring between physical offices that don’t have a VPN connection, the print job might travel outside your local network, but it is fully encrypted at rest and in motion using HTTPS protocols.Enabling and disabling the Cloud Node is as simple as switching a toggle. Either way, your print documents are fully encrypted. But if you want to ensure that your print job data never, ever leaves your network(s), just leave the Cloud Node turned off.
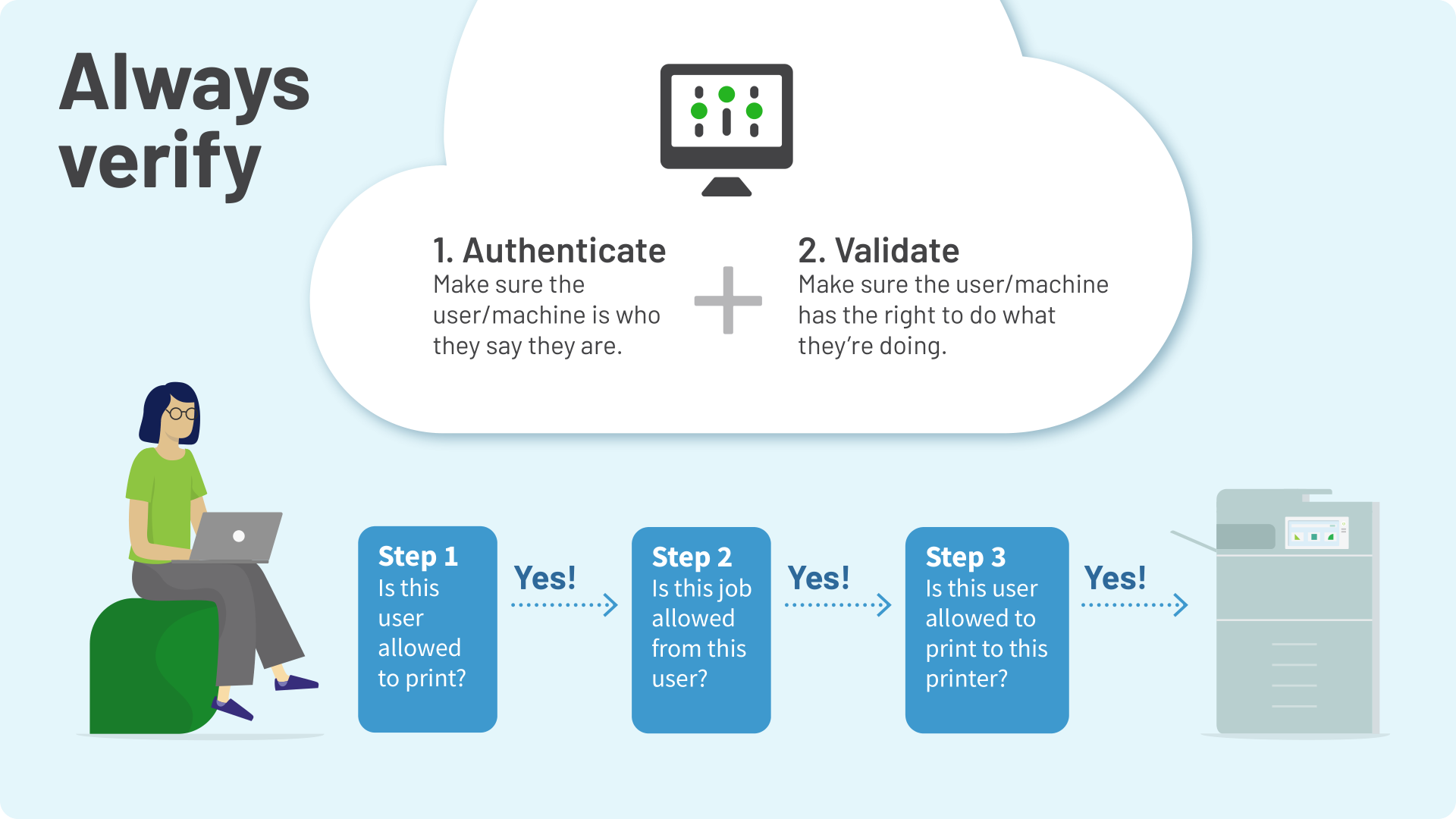
Building trust in your network with the “always verify” principle
PaperCut Hive and PaperCut Pocket ’s Edge Mesh technology was designed using the “always verify” principle.
“Always verify” means every time a print job is submitted into the Edge Mesh, the user, their client, and any edge nodes are always authenticated and validated. No user, client, or device is automatically trusted. Print permission isn’t assumed just because you’re on the network.
Every user, computer, and printer is explicitly approved by system administrator action to join the local Edge Mesh. Users (or malicious actors) can’t “just plug in”; a pairing process is required.
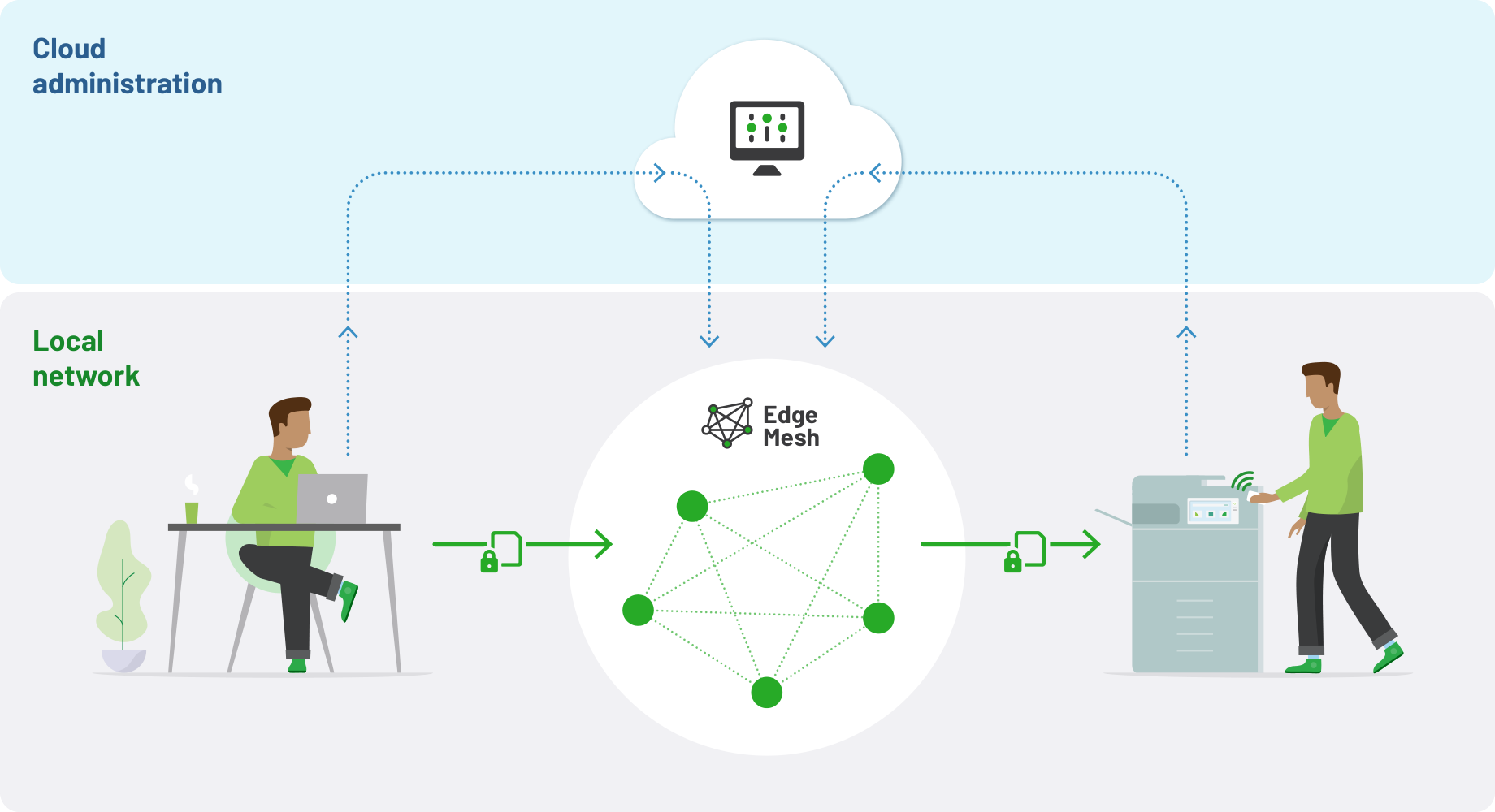
Fully encrypted print job paths
Any data transfer between any component of the system is encrypted. Let’s look at the end-to-end flow of a print job: the job on the client device is encrypted before sending to the Edge Mesh.
The document stored in the Edge Mesh is encrypted with a multi-part key, and the print job is encrypted at the last possible point. Likewise, an administrator using the admin console is always verified and uses a HTTPS/SSL connection.
Secured data at rest and in motion
At rest - After you click print, if the job needs to be temporarily stored prior to secure print release, it is securely encrypted using AES256-GCM. While a print job is sitting on an edge node waiting to be released, it’s secured with a 3-part encrypted key:
- A key belonging to the print job itself
- A key belonging to the edge node’s identity
- A key linked to the organization’s account
Invalidating any one of these keys invalidates the ability to decrypt the print job.
In motion - All print documents and their attributes are transmitted around your network with a secure HTTPS channel. If you have optionally enabled the cloud node, of course the job is also encrypted in transit.
Encryption occurs at the client print device (e.g. a mobile device or laptop) into the Edge Mesh, and if transferred within the Edge Mesh is also encrypted. When the document finally needs to be delivered to a physical printer, it is also encrypted using the IPPS print protocol if supported by the printer.
For more information about print security and best practises related to our cloud-native products, visit the PaperCut Hive and PaperCut Pocket manual.
PaperCut MF hosted in the cloud
Both the private-hosted and self-hosted models of PaperCut MF are designed for individual organizations (single tenants) with more traditional systems comprising on-site hardware like Active Directory servers and door security databases. The private cloud instance (VM) and self-hosted servers are not accessible from the public internet. For many businesses this solution is the right balance between the benefits of security and the cloud.
For cloud hosting of PaperCut MF, whether your host site is a Private Cloud or a Virtual Private cloud, following best practise your print environment is generally connected to the cloud-hosted PaperCut server via a secured, encrypted VPN tunnel (e.g. IPSec, or a dedicated connection such as Azure Express Route or AWS Direct Connect. Usually deployments are built on top of the isolation features provided by major cloud hosting providers such as Microsoft Azure, AWS, and Google GCP.
This tunnel ensures end users can print as if the PaperCut MF application was hosted locally on-prem, while ensuring secure and restricted access to the hosted service. Put simply, your private-hosted instance of PaperCut MF is isolated from the public internet. Those pesky data buccaneers can’t lay their dirty mitts on your print jobs.
Some customers with high print volumes may also consider a hybrid setup where a local print server is set up on prem to handle the load but the PaperCut application server and database sits in the cloud. This setup offers a pragmatic approach balancing privacy, performance, bandwidth, and cloud convenience (your print job data doesn’t leave your local network).

PaperCut MF was built as a web service with remote browser administration, which is perfect for private cloud deployment. Its web-based UI administration makes it secure and tolerant of network latency.
PaperCut uses secure http-based communications protocols on defined ports for relatively simple security configuration of firewalls and VPNs. This in turn means it’s quick and easy to build a low-latency print environment within your private cloud environment.
Private hosting can curtail hardware failure, which is a major advantage of this implementation. In their nature, infrastructure providers usually have banks of servers and data centers. The major cloud providers work hard to ensure that a hardware crash at their end is transparently handled and in most cases potentially unnoticeable. This means the uptime of PaperCut MF in the cloud is often higher than what you see running on your own local hardware.
Private hosting does mean that you need a reliable internet connection, or at least, an internet disruption should have minimal impact on your business operations. There should also be contingencies (like back-up links, or an Internet Service) for unreliable internet connections. Whether hosting PaperCut MF in the cloud is the right fit depends on weighing up the benefits of automatic failover against reliability considerations.
For more information on private cloud hosting of PaperCut MF, visit our Knowledge Base.
Cloud Print with Mobility Print
Printing from mobile devices such as smartphones, tablets, and Chromebooks, is becoming increasingly important in modern hybrid working practises. This often extends to printing offsite and collecting onsite (e.g. printing from home and collecting in the office, also referred to as remote/off-network printing). This is where Mobility Print and its cloud features shine (either Mobility Print running under PaperCut MF or the Mobility Print standalone.
PaperCut’s Mobility Print’s Cloud Print feature is built on top of a secure-by-default, peer-to-peer communication technology called WebRTC. This means that all data transmitted from the print client to your Mobility Print server is encrypted and where possible transferred directly (not via an intermediate server).Only the end points can access the data. It is completely end-to-end encrypted using DTLS protocols. The data is never stored on a public cloud server.
For more about Cloud Print security and privacy in Mobility Print, read our manual.
Secure by default
Security is not something new to PaperCut’s customers. However, the priority of security has changed over the last 20 years. Today, acronyms like GDPR, CCPA, HIPAA, HITECH, and PCI-DSS naturally make their way into a CIO’s everyday compliance conversations.
The increased focus on security, data sovereignty, and privacy is only a good thing, and has been a first and foremost concern of PaperCut’s development teams since our early days. Why? PaperCut’s first version of software was released in the education market and we all know students like to hack!
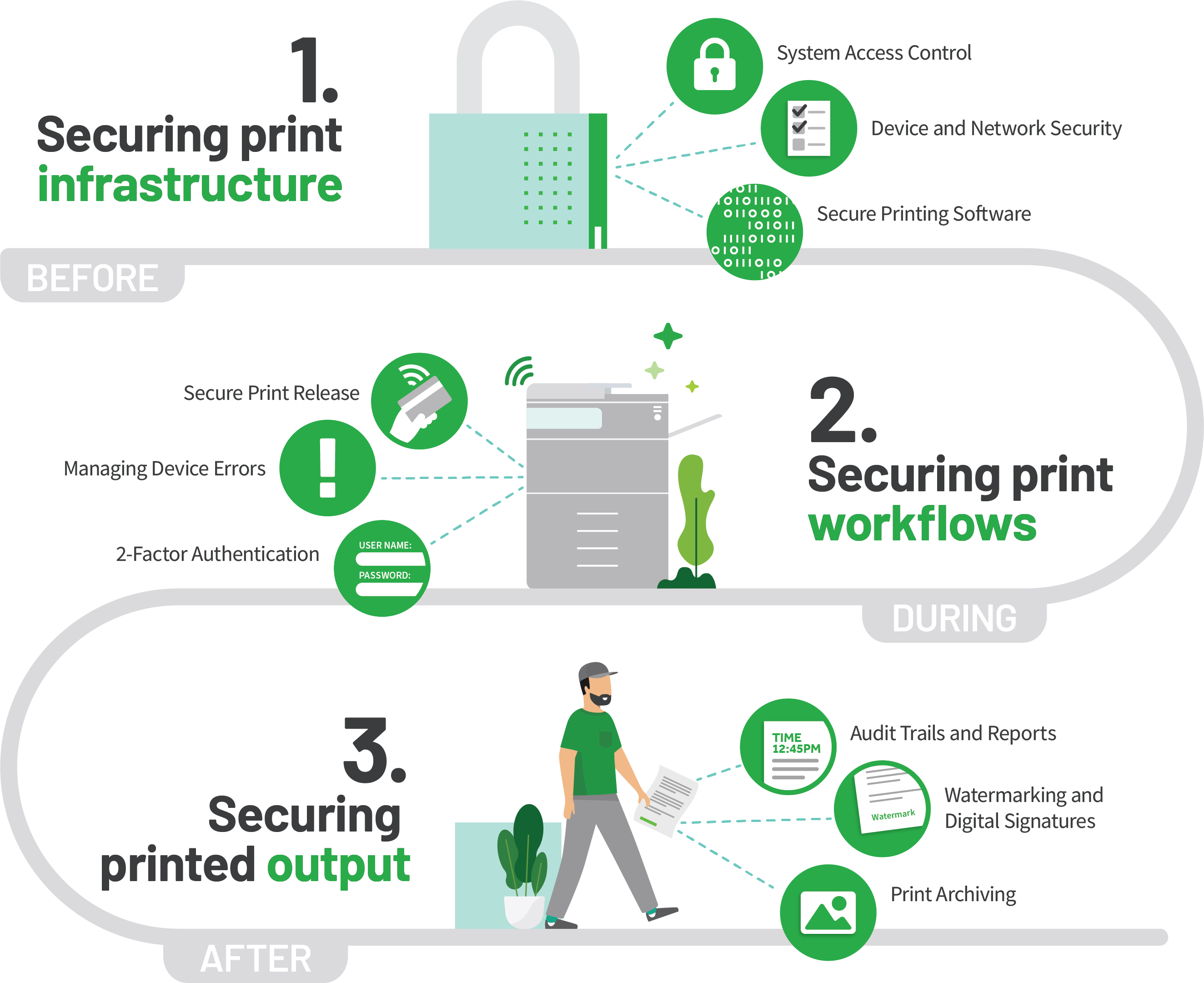
Integral to our philosophy is the notion that the document needs to be protected throughout its entire lifecycle: before, during, and after printing occurs.
For example:
- Before - e.g. who has access and when
- During - e.g. secure print release, and encrypted transfer
- After - e.g. watermarking, digital signatures, and print job archiving
This philosophy is applied across our entire product suite from on-prem to cloud solutions.
In relation to our fully-hosted (multi-tenant SaaS) solutions, PaperCut Hive and PaperCut Pocket, the Edge Mesh platform was built from scratch specifically for the public cloud. Cloud level security features were baked in from the first line of code day one.
Want to know more?
Check out these links: