Syncing PaperCut users with Windows Active Directory is possible when you have a Windows PaperCut server joined to an Active Directory domain.
If your primary PaperCut server is macOS or Linux, it’s still possible to synchronize users from Active Directory. However, you’ll need to connect using the LDAP sync source and set the LDAP Server Type to Microsoft Active Directory. See Synchronize user and group details with LDAP for steps.
The advantages over the Windows Standard option include the following:
- Allows use of Active Directory organizational units.
- Supports nested groups for simplified user management.
- Allows importing users from other trusted Active Directory domains.
PaperCut NG/MF’s Active Directory integration is performed at a native level and supports advanced features such as nested groups and OUs.
To synchronize your user data with Active Directory:
- Set the primary sync source
- Add card/identity numbers
- Set the secondary sync source (optional)
- Set the sync options
How PaperCut user authentication works with a Windows Active Directory sync source - NTLM or Kerberos
The application’s user authentication depends on Microsoft NTLM protocol, also known as Windows Challenge/Response. PaperCut NG/MF versions 24.1.3 and later also support the Kerberos authentication protocol.
NTLM overview
NTLM uses an encrypted challenge/response protocol to authenticate a user without sending the user’s password over the wire. Instead, the App Server requesting authentication must perform a calculation that proves it has access to the secured NTLM credentials.
Interactive NTLM authentication with PaperCut involves three systems:
- User client system - embedded device, Mobility client, PaperCut software client, user web pages
- App Server - to which the user is requesting authentication
- domain controller - where information related to the user’s password is kept.
NTLM authentication workflow
The PaperCut authentication workflow is otherwise known as non-interactive authentication.
The following authentication workflow is adapted from the article Microsoft NTLM . The first step provides the user’s NTLM credentials
- A user accesses a client system (as described above) and provides a user name and password. The client system sends the user name to the App Server in plaintext. However, keep in mind that PaperCut client systems automagically upgrade their authentication connections to the App Server from HTTP to HTTPS, so passwords will not traverse the network un-encrypted with one exception: authentication attempts through user or admin webpages using the
HTTP:// URLinstead ofHTTPS://. In any case, the App Server computes a cryptographic hash of the password and discards the actual password. - The domain controller generates a 16-byte random number, called a challenge or nonce, and sends it to the App Server.
- The App Server encrypts this challenge with the hash of the user’s password and returns the result to the Domain Controller. This is called the response.
- The App Server sends the following three items to the domain controller: User name, Challenge and Response
- The domain controller uses the user name to retrieve the hash of the user’s password from the Security Account Manager database. It uses this password hash to encrypt the challenge.
- The domain controller compares the encrypted challenge it computed (in step 5) to the response computed by the App Server (in step 3). If they are identical, authentication is successful.
Kerberos overview
Kerberos uses a ticket-based system to authenticate a user without sending the user’s password over the wire. Instead, the App Server requesting authentication verifies a ticket presented by the user, proving the user has been authenticated by a trusted Key Distribution Center (KDC).
Interactive Kerberos authentication with PaperCut involves three systems:
- User client system - embedded device, Mobility client, PaperCut software client, user web pages.
- App Server - to which the user is requesting authentication.
- Key Distribution Center (KDC) - where information related to the user’s password (used to issue tickets) is kept.
The user client system obtains a ticket granting ticket (TGT) from the KDC. When the user attempts to access the App Server, the client requests a service ticket for the App Server from the KDC using the TGT. The KDC issues this service ticket, which the client then presents to the App Server. The App Server verifies this ticket.
The PaperCut authentication workflow using Kerberos, like NTLM in PaperCut, is also considered a form of non-interactive authentication as the user does not need to repeatedly enter their credentials for each service request after initially obtaining their TGT.
Kerberos authentication workflow
The authentication workflow below is adapted from the article Microsoft Kerberos .
- User requests a TGT.
A user accesses a client system and provides their username and password. The client system sends this information to the KDC. The KDC is a trusted server that manages Kerberos authentication. - The KDC authenticates the user.
The KDC verifies the user’s credentials (typically by checking against a database like Active Directory). If the credentials are valid, the KDC issues a TGT to the client. This TGT acts as a temporary credential for the user. - The client requests a service ticket.
When the user attempts to access the App Server, the client uses the TGT to request a service ticket from the KDC. This ticket is specific to the App Server. - The KDC issues a service ticket.
The KDC verifies the TGT and issues a service ticket for the App Server. This ticket is encrypted and can only be used by the App Server. - The client presents the service ticket to App Server.
The client presents the service ticket to the App Server. - The App Server authenticates the user.
The App Server decrypts the service ticket using its own secret key. If the ticket is valid, the App Server authenticates the user and grants access.
Configuring authentication modes for Kerberos in PaperCut NG/MF
There are two authentication codes:
-f(Force modern authentication only)-l(Legacy authentication only)
-f (Force modern authentication only)
Use this option to ensure that PaperCut NG/MF only uses only modern authentication methods, such as Kerberos, and does not fall back to NTLM.
When to use
- Your network security policies prohibit NTLM authentication.
- You want to enforce stricter security measures by relying solely on Kerberos.
Example usage
auth.exe -f
-l (Legacy Authentication Only)
Use this option to force PaperCut to authenticate using legacy methods, such as NTLM, without attempting Kerberos authentication.
When to use
- Kerberos authentication is causing issues in your environment.
- You need PaperCut to function as it did before Kerberos authentication attempts were introduced.
Example usage
auth.exe -l
Configuring authentication in PaperCut MF
The authentication mode can be configured in PaperCut MF by adding the desired option to the global config key auth.source.config-arg using the l or f lettering as shown above.
Set the primary sync source
-
Select Options > User/Group Sync. The User/Group Sync page is displayed.
-
In the Sync Source area, in Primary sync source, select Windows Active Directory.
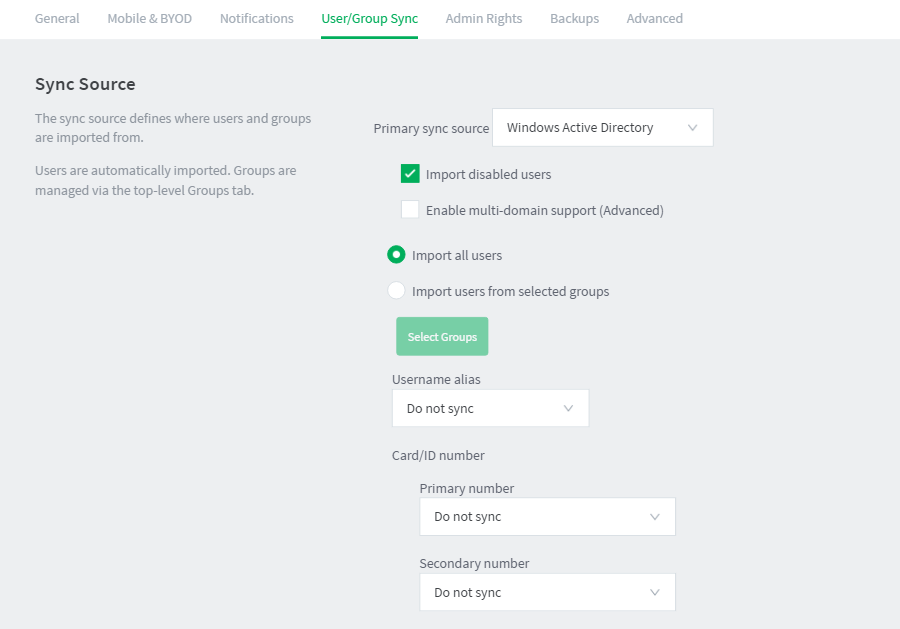
-
Complete the following fields as required:
-
Import disabled users— If set, all users, including disabled accounts are imported from the domain. In an education environment, select this option as student accounts are sometimes disabled for disciplinary actions, so removing the account from PaperCut NG/MF is not appropriate. This option is normally off by default.
-
Enable multi-domain support—Select this option for larger sites running multiple trusted domains. For example, in an education environment it is common to have separate domains for students and staff/teachers with a one-way trust relationship. This option can bring in groups, OU’s, and users from both domains.
The list of domains is semicolon separated (
;). This list should contain the name of the domains in DNS dot notation, and should include the name of the current domain if you want to import from this domain.Trust domain relationships is a complex area. Click Test to verify that the settings result in the desired behavior. The total number of user accounts is a good measure.
-
-
Select the users to import:
- Import all users
- Import users from selected groups—If you select the option, click Select Groups; then select the groups/OUs you want to import. This option is useful if the domain contains old users or users who do not print.
Synchronizing Card/ID Numbers
Card and ID numbers are used as an alternative to usernames/passwords for authentication at software Release Stations, or at hardware terminals attached to photocopiers. The card/ID number can also be searched in the user quick-find on the User List page. PaperCut can synchronize this information from a field in your directory.
Detailed information can be found on our page: Synchronize Card/Identity Numbers from a directory .
Set the secondary sync source (optional)
Enabling a secondary sync source allows PaperCut to merge the results from two independent sources. Examples of where this is useful include:
- A school with an Active Directory domain for the majority of users and a separate LDAP server that is used and managed by one department.
- An organization with a new LDAP server and an old legacy LDAP server with separate but unique users who have not been migrated to the new server.
- A university with an Active Directory for the Windows student workstations and an Open Directory for the staff Mac workstations.
When enabled, PaperCut queries both sources to find users and groups. Usernames are treated as globally unique, so the same username existing in both sources is treated as the same user (in this case, the details for the user are merged, with the primary sync source taking priority). If there is an error connecting to or synchronizing against either source, then no actions takes place.
To set a secondary sync source:
- In the Secondary Sync Source (Advanced) area, select the Enable secondary sync source check box.
- Complete the secondary sync source details as described above. These fields are the same as those for the primary sync source.
Set the sync options
The options listed in the Sync Options area control how the synchronization will take place.
-
In the Sync Options area, select any of the following options as appropriate:
-
Update users’ full-name, email, department and office when synchronizing—if a user’s details in PaperCut do not match those in the synchronization source, update the details in PaperCut NG/MF.
-
Import new users and update details overnight—synchronization automatically occurs each night at approximately 12:55am. This option never deletes users from PaperCut.
-
Delete users that do not exist in the selected source—deletes users from PaperCut if they no longer exist in the selected synchronization source.
This option affects only users added via the synchronization source (for example, the domain) and does not delete Guest and anonymous user management . Users that do not exist in the Sync source are deleted only when you manually synchronize (click Synchronize Now).
This option does not delete users when automatically synchronizing overnight.
-
-
To test the operation, click Test Settings. A Testing sync settings popup dialog box displays the details of users and user groups that will be modified (updated, added, or deleted) when the actual sync operation is run.
-
Click Apply.
Syncing a secondary email address from Active Directory
In order to have PaperCut NG/MF sync a secondary email address from Active Directory for your users, the trick is to set it up to point to a custom field in AD.
- Log in to the PaperCut admin web interface.
- Navigate to Options > Actions > Config editor (advanced).
- Use Quick find to search for the
user-source.ad.other-emails-fieldconfig key. - In the blank field in the Value column, enter the name of the Active Directory field where your users secondary email addresses are stored. You can use any unused attribute of your choosing in AD (or even create your own). A common selection is to re-use the pager field as there is not much call for pagers these days so it’s a safe choice! Do note that the entry must match the name of the field in AD exactly; it’s case sensitive, and any variation from the exact name of the field will cause the syncing of their additional email addresses to fail.
- Click Update next to the Value field to apply the change.
Now the next time a user sync takes place, it should pull the email addresses of your users stored in the specified AD field into the ‘Other emails’ field for that user:

Importing user Office and Department fields from non-standard fields in Active Directory
When using PaperCut’s native Active Directory integration, the user’s Office and Department fields are imported from the standard Active Directory office and department fields. In some organizations they store this information in alternate fields in Active Directory, or use the Company attribute instead, and would like these to be imported into PaperCut for reporting purposes.
There currently isn’t a way to change which field is imported using the standard Active Directory source, however you can use PaperCut’s LDAP integration to retrieve this information.
PaperCut’s LDAP integration can import users, authenticate users, etc in the same way as the native Active Directory integration. The only downside of using the LDAP integration is that you cannot make use of AD nested groups.
Configure PaperCut to import the office/department from a different AD field
- Open the Admin interface and login as an admin user.
- Select the Options section, then the User/Group Sync tab.
- Select the LDAP user source. For detailed instructions on LDAP setup see the manual
- Apply the changes and perform a test to ensure your LDAP configuration is working as expected.
At this point PaperCut will still import the office/department from the standard AD fields. To change the field the PaperCut uses requires some configuration of PaperCut’s LDAP import settings. These settings are described in the manual here .
You can set the ldap.schema.user-department-field or the ldap.schema.user-office-field fields to change the AD field that is retrieved. If you’re unfamiliar with editing config keys, see
Using the advanced config editor
.
Troubleshooting AD sync issues
For more help in resolving AD sync issues, check out our Knowledge Base articles:




Comments